Embedded Scripting in RN4871 - Turn Led on Connect and off Disconnect
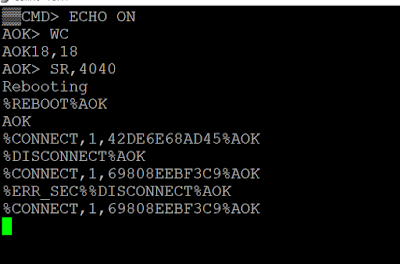
RN4871 supports embedded scripting: Steps to turn LED On during connection and Off during disconnection: 1. Type '$$$' to enter command mode 2. Type '+' for ECHO back the commands we typed 3. Type 'WC' to clear the script 4. Type 'WW' to add a new script. Type the below following: @PW_ON SW, 0A, 00 #Remove special functionality on Pin 12 SW, 0B, 00 # Remove special functionality on Pin 13 |O,18,00 #TURN LED ON |O,18,18 #TURN LED OFF @CONN |O,18,00 #TURN LED ON @DISCON |O,18,18 #TURN LED OFF 5. Type ESC to come out of script to command mode 6. Type 'SR,4040' to start the script to run after power on and with no prompt 7. Type 'R,1' to reboot the module 8. Connect Male to Female Cable from P12 (J11) to any pin on JP5 When you connect from Phone, the LED will be ON and when you disconnect it will be OFF