POSIX Capabilities Part 3 - CAP_SYS_BOOT - Allow Non-root user to reboot
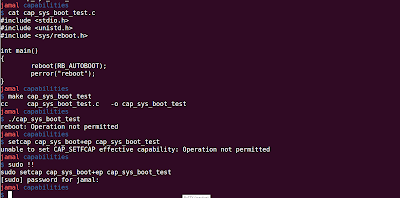
Linux provide 'reboot' api to allow user to perform a reboot from Linux Code. #include <unistd.h> #include <sys/reboot.h> int reboot(int cmd); reboot(RB_AUTOBOOT); will print the message "Restarting system." and reboot will be performed. If a non-root user tries to perform this, it will fail with permission denied error. Now, if we run cap_sys_boot_test, the system will reboot when run with non-root user.