Debugging Linux Kernel using ftrace Part21 - kernel function profiling
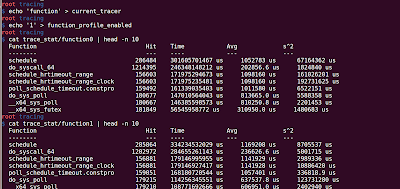
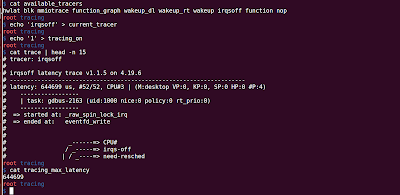
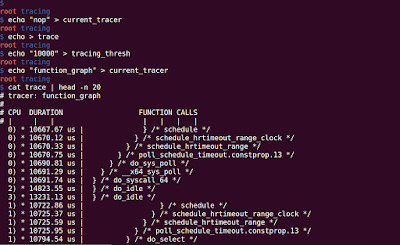
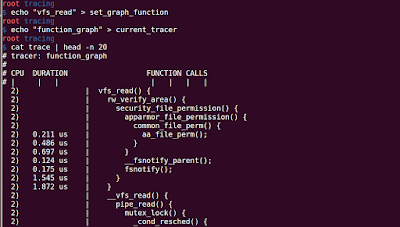
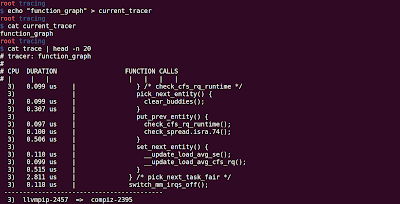
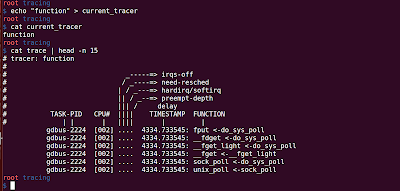
From Wikipedia, function profiling provides you the following : Space or Time Complexity of a Program Usage of Particular Instruction Frequency and duration of function calls ftrace can provide you the following function profiling information using 'function_profiling_enabled' file. Frequency of function calls (When the tracer is 'function') Duration spent in each function calls (When the tracer is 'function_graph') Steps for Function profiling: 1. Enable the function tracer: 'function'/'function_graph' echo 'function' > current_tracer 2. Enable the function profiling: echo '1' > function_profiling_enabled To observe the results look into '/sys/kernel/tracing/trace_stat' folder. You will observe a lot of file with the following name: function<number> (e.g. function0, function1,...), where number represents the core on which the function is executing. So, if you have 4 Processors, funct...