Debugging Linux Kernel Using SystemTap Part-9 - Probing interrupts
In Linux, do_IRQ() function is called on each interrupt, which calls handle_IRQ_event(), which finally calls the handlers registered with request_irq() call.
Systemtap already provides scripts/tapset for irq (/usr/local/share/systemtap/tapset/linux/irq.stp)
Script:
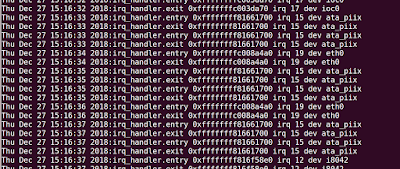
Output:
Notes:
1. symname function will print out the raw address
2. kernel_string will get the string at the address passed as argument
3. pn() returns the active probe name
1. symname function will print out the raw address
2. kernel_string will get the string at the address passed as argument
3. pn() returns the active probe name


Comments
Post a Comment